What is JWT (JSON Web Token)?
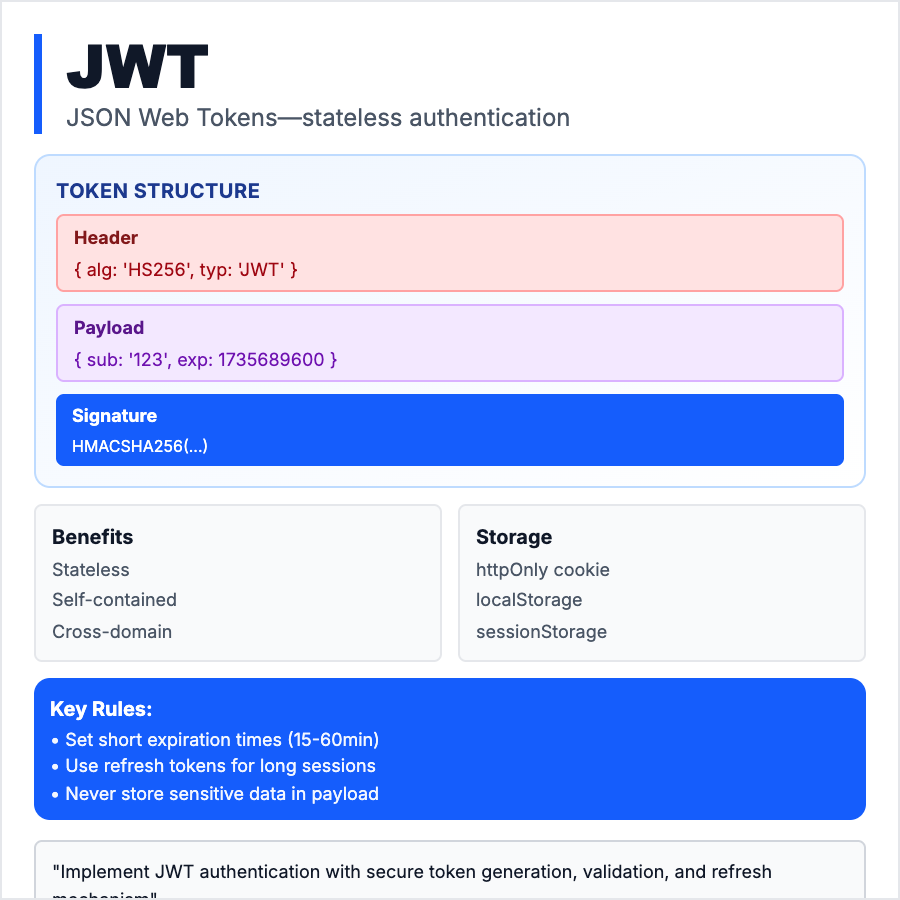
JWT (JSON Web Token) is a compact, self-contained token format used for authentication and authorization. It's a signed piece of data (usually JSON) that proves a user is authenticated without needing to check a database on every request. JWTs contain claims (user ID, roles, expiration) and are cryptographically signed so you can trust them. Common in API authentication.
When Should You Use This?
Use JWTs for stateless authentication in APIs, microservices, or SPAs where you don't want to hit a database on every request. Perfect for mobile apps, serverless functions, or distributed systems. JWTs work well with OAuth—the OAuth flow returns a JWT access token. Don't use JWTs for session management in traditional web apps (use httpOnly cookies instead).
Common Mistakes to Avoid
- •Storing JWTs in localStorage—XSS attacks can steal them; use httpOnly cookies
- •Not validating signatures—always verify the token is signed with your secret key
- •Setting long expiration times—JWTs can't be revoked; keep them short (15min) + use refresh tokens
- •Putting sensitive data in JWTs—they're base64-encoded, not encrypted; anyone can read them
- •Not using HTTPS—JWTs sent over HTTP can be intercepted (man-in-the-middle attacks)
Real-World Examples
- •Auth0—issues JWTs for user authentication, apps validate the signature without calling Auth0
- •Firebase—uses JWTs for authentication across web, mobile, and backend
- •Stripe API—uses JWT-like bearer tokens for API authentication
- •GitHub API—OAuth returns a JWT-based access token for API calls
Category
Cybersecurity
Tags
jwtjson-web-tokenapi-authenticationbearer-tokensecurity