What is MFA (Multi-Factor Authentication)?
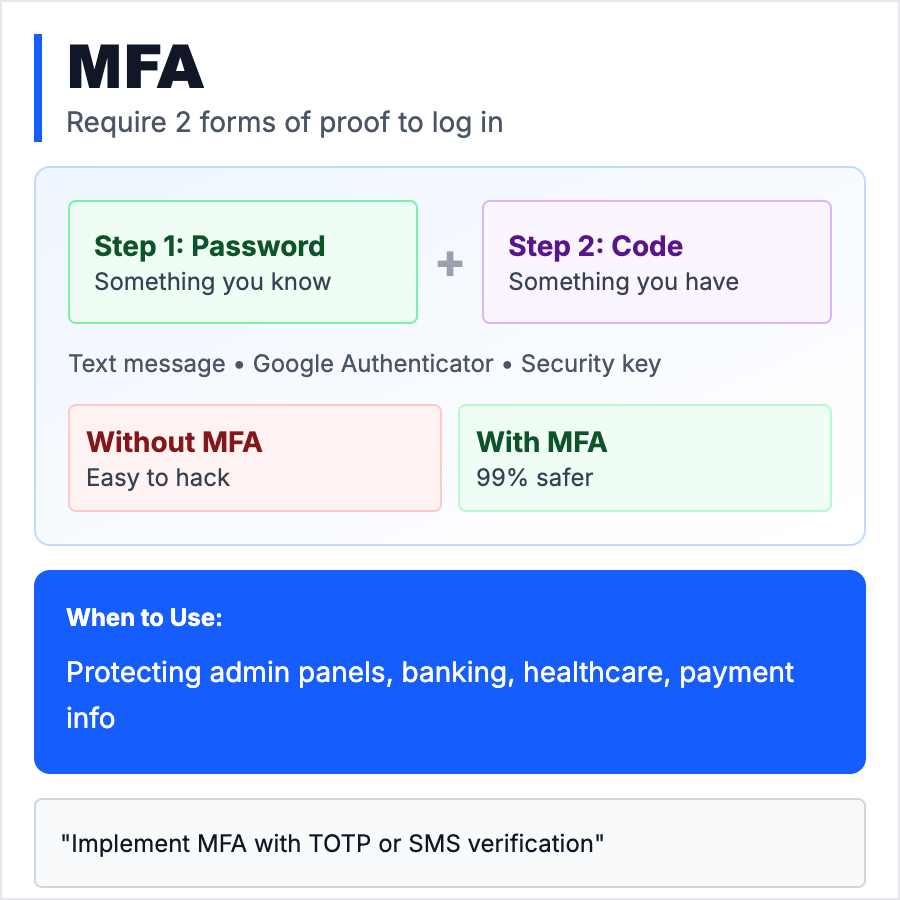
MFA (Multi-Factor Authentication) requires users to prove their identity with two or more factors: something they know (password), something they have (phone, hardware key), or something they are (fingerprint, face). Most common is 2FA (two-factor): password + SMS code or TOTP app (Google Authenticator, Authy). Dramatically reduces account takeovers from stolen passwords.
When Should You Use This?
Require MFA for high-value accounts (admins, financial data, healthcare, enterprise customers). Offer MFA as an option for all users. For B2B SaaS, MFA is often required for SOC 2 compliance or enterprise deals. Use TOTP (authenticator apps) over SMS—SMS can be intercepted. For highest security, support hardware keys (YubiKey, WebAuthn).
Common Mistakes to Avoid
- •Only supporting SMS codes—SMS is vulnerable to SIM-swapping attacks; use TOTP or WebAuthn
- •Forcing MFA on everyone immediately—let users opt-in first, then gradually enforce for sensitive actions
- •Not providing backup codes—users lose access if they lose their phone; generate 10 one-time backup codes
- •Poor recovery flow—if MFA fails, users get locked out; have a secure recovery process (admin override, ID verification)
- •Ignoring UX—MFA is friction; only prompt when necessary (new device, sensitive action, periodic re-auth)
Real-World Examples
- •GitHub—requires MFA for all developers who contribute to high-profile projects
- •AWS—enforces MFA for root accounts and IAM users with sensitive permissions
- •Coinbase—requires MFA for all accounts (crypto exchanges are high-value targets)
- •Notion—offers MFA for enterprise customers to meet compliance requirements
Category
Cybersecurity
Tags
mfa2famulti-factor-authenticationtotpsecuritywebauthn