What is Password Policies?
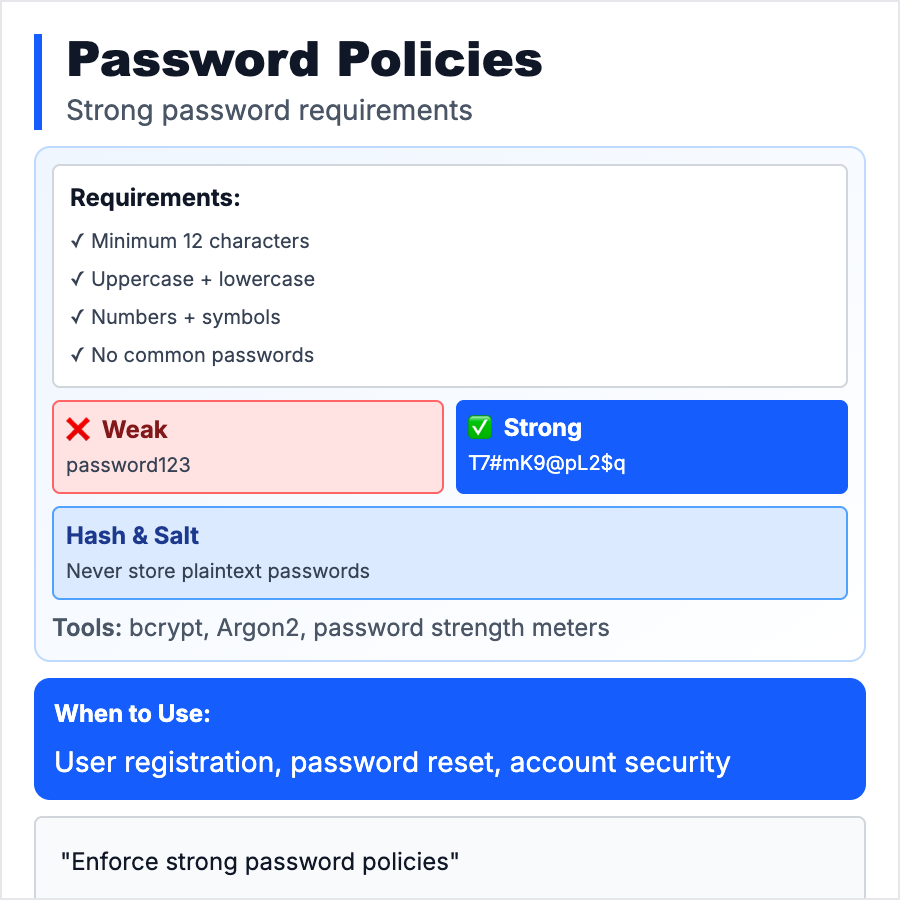
Password Policies define rules for password creation, storage, and rotation to prevent weak passwords and account takeovers. Modern best practices: require 8+ characters, allow passphrases, no forced complexity (Password123! is weak), use bcrypt/Argon2 for hashing, check against breach databases (Have I Been Pwned), offer password managers. No forced rotation (leads to weaker passwords).
When Should You Use This?
Enforce password policies on all auth systems. Minimum 8 characters (prefer 12+), check against common passwords (123456, password), use bcrypt with high cost factor (10-12 rounds). Offer "show password" toggle to reduce typos. Support passkeys/WebAuthn as a better alternative. For enterprise, offer SSO to avoid password management entirely.
Common Mistakes to Avoid
- •Forcing complexity rules—P@ssw0rd! satisfies requirements but is weak; length matters more
- •Storing passwords in plaintext—always hash with bcrypt, Argon2, or PBKDF2
- •Using weak hashing (MD5, SHA1)—too fast to hash = easy to brute-force; use bcrypt
- •Forced password rotation—users create weaker passwords (Password1 → Password2); only rotate after breach
- •Not rate limiting login attempts—attackers brute-force passwords; limit to 5 attempts per minute
Real-World Examples
- •1Password—enforces strong master password, uses PBKDF2 + AES-256 for storage
- •GitHub—checks passwords against Have I Been Pwned, warns users of breached passwords
- •Google—requires 8+ characters, checks against common passwords, offers passkeys
- •Auth0—built-in password policies with breach detection and configurable requirements
Category
Cybersecurity
Tags
password-policiespassword-securitybcryptpassword-hashingauthentication