What is Encryption?
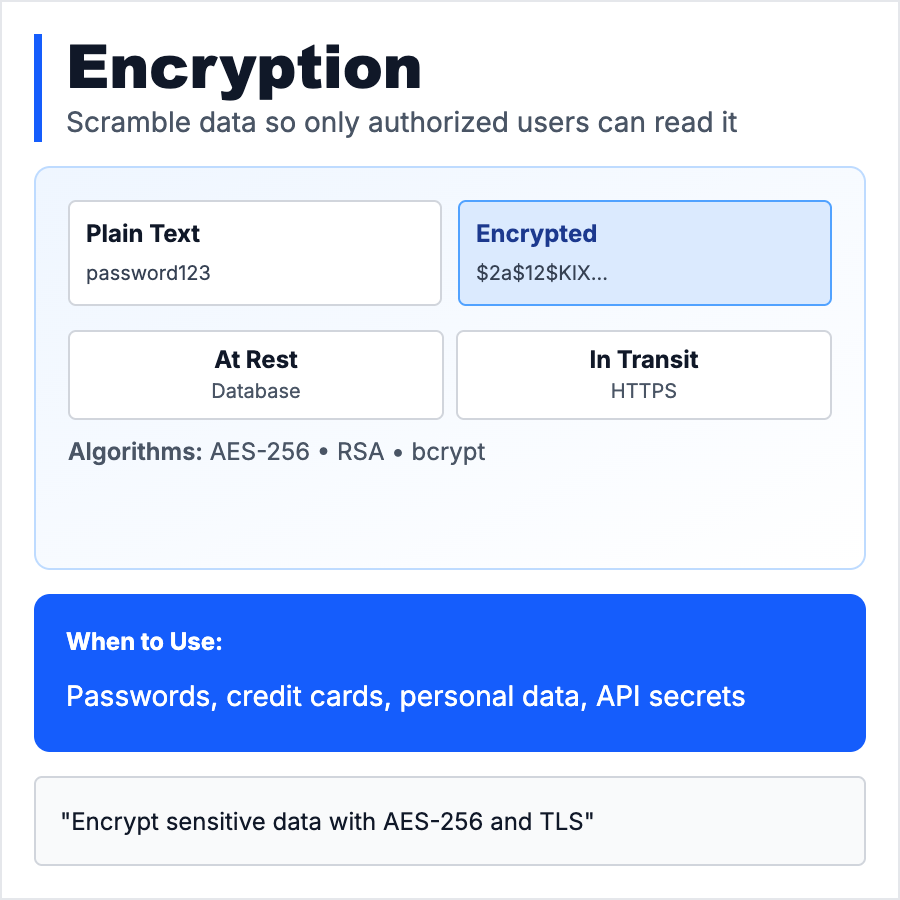
Encryption transforms readable data into scrambled ciphertext that can only be decrypted with the right key. Two types: encryption at rest (data stored in databases, files) and encryption in transit (data sent over networks). Use HTTPS/TLS for transit, AES-256 for at rest. Encryption protects data from breaches, eavesdropping, and unauthorized access.
When Should You Use This?
Encrypt ALL data in transit with HTTPS/TLS—no excuses. For sensitive data at rest (passwords, PII, financial data), use AES-256 encryption. Use bcrypt/Argon2 for password hashing (not AES). For end-to-end encryption (E2EE), only users have keys—not even you can decrypt (Signal, WhatsApp). Most cloud providers (AWS, GCP) offer automatic encryption at rest.
Common Mistakes to Avoid
- •Not using HTTPS—data sent over HTTP can be intercepted; use TLS everywhere
- •Encrypting passwords with AES—use password hashing (bcrypt, Argon2) not encryption
- •Storing encryption keys in code—use secret managers (AWS Secrets Manager, HashiCorp Vault)
- •Using weak algorithms—avoid MD5, SHA1, DES; use AES-256, SHA-256, RSA-2048+
- •Forgetting about key rotation—rotate encryption keys periodically to limit breach impact
Real-World Examples
- •WhatsApp—end-to-end encryption for messages (only sender/receiver can decrypt)
- •AWS S3—automatic AES-256 encryption at rest for all stored files
- •1Password—uses AES-256 + PBKDF2 to encrypt passwords, keys stored locally
- •Signal—pioneered E2EE for messaging, open-source protocol used by WhatsApp, Skype
Category
Cybersecurity
Tags
encryptionaestlshttpsdata-securitye2ee