What is SQL Injection Prevention?
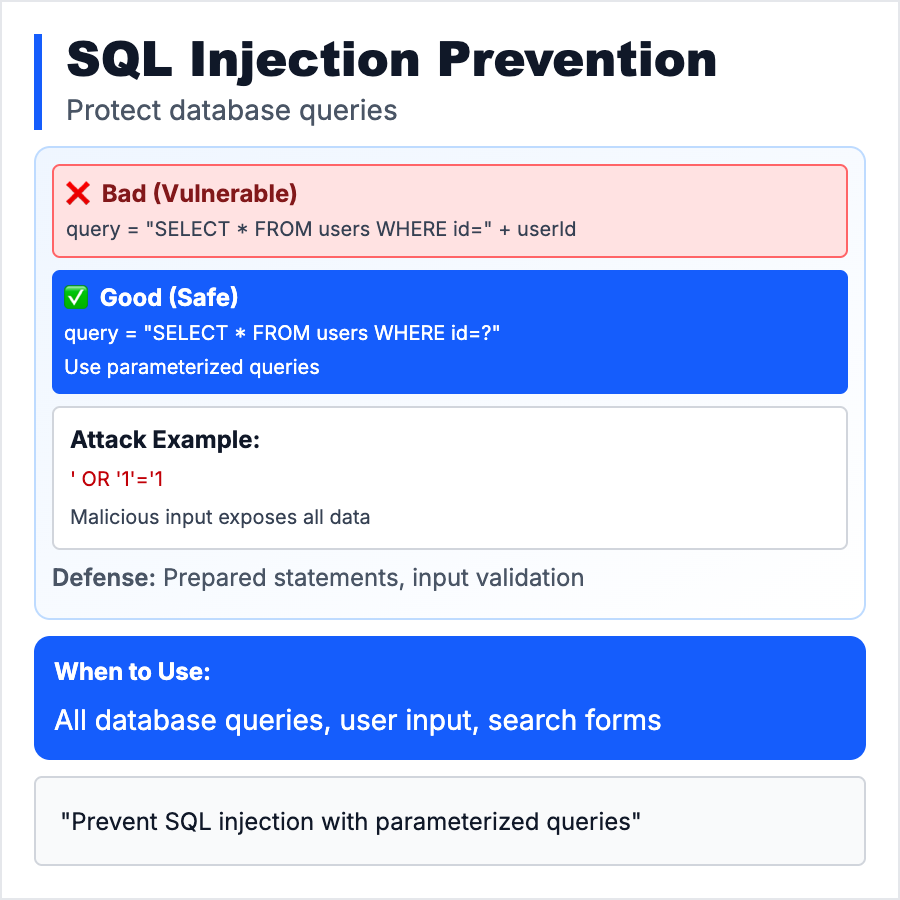
SQL Injection is an attack where malicious SQL code is injected into input fields, tricking your database into executing unintended commands—stealing data, deleting tables, or bypassing authentication. Happens when you concatenate user input into SQL queries. Prevent with parameterized queries (prepared statements) that treat input as data, not code.
When Should You Use This?
Prevent SQL injection in every app that uses a database. Never concatenate user input into SQL strings—always use parameterized queries or ORMs (Prisma, Drizzle, SQLAlchemy, ActiveRecord). Test with payloads like ' OR 1=1 --, '; DROP TABLE users; --. Use database permissions to limit damage (read-only user for SELECT queries).
Common Mistakes to Avoid
- •String concatenation in SQL—SELECT * FROM users WHERE id = "$id" is vulnerable; use parameterized queries
- •Trusting input validation—attackers bypass frontend checks; sanitize on backend
- •Using ORMs incorrectly—raw queries in ORMs can still be vulnerable; use ORM query builders
- •Not limiting database permissions—app user shouldn't have DROP TABLE access
- •Forgetting about NoSQL injection—MongoDB, Firestore also vulnerable to injection; validate input
Real-World Examples
- •Heartland Payment (2008)—SQL injection stole 130M credit cards, $200M+ in damages
- •Sony (2011)—SQL injection exposed 77M PlayStation accounts
- •Prisma ORM—uses parameterized queries by default, preventing SQL injection
- •SQLMap—penetration testing tool that automates SQL injection attacks
Category
Cybersecurity
Tags
sql-injectionsql-securityparameterized-queriesdatabase-securityinjection-attacks